Project/VLAN
Introduction
This project is a description of a practical implementation of using VLANs in a network to avoid certain problems related to multicast packets. It is by no means a complete explanation of VLANs and how they should and could be implemented. If you have IPTV at your home, and experience problems with your current network setup, VLAN implementation could be the solution.
Old situation
IPTV is a solution for offering TV reception over a computer network. This seems like a good idea, because with the introduction of digital TV, such as DVB(-S, -C and -T), the TV signal is no longer analog, but merely a digital data stream that a suitable TV can decode into video and audio, and all other supporting data streams (subtitles, electronics program guide, text TV and so on). With service providers offering fiber-to-the-home, IPTV is looking to be an answer for these companies to offer a complete service (next to telephone and internet service).
So the IPTV box is connected by a normal Ethernet connection, such as a CAT5 cable. Due to the fact that many homes are not fitted with these cables all over, often a powerline adapter is used to carry the signal over the standard 230V power lines. While this works kind of OK, there are drawbacks to this solution.
- Powerlines are unshielded. Your whole house becomes an antenna, making the connection inherently unsecure.
- This system is very susceptible to interference. If you have a microwave oven, or turn on other high current loads, the connection may suffer.
- The more people in the area use this system, the worse your connection will be. Just like Wi-Fi, the powerline interface can become crowded.
Another solution is to use separate cables. This is a good solution, but if you already have loads of CAT5E wiring throughout your home, this seems redundant. Therefore, you would be tempted to simply connect the IPTV boxes to your existing network. This is the start of heaps of misery and the cause for looking into VLANs. IPTV communicates with UDP-IP communication, over multicast packets. Every switch will recognize these packets and will broadcast them over the entire network, being the nature of multicast packets. Your whole network will get swamped with mostly useless packets, and inhibits the proper communication of other devices!
Even the use of gigabit switches will not help, because all these switches support a maximum amount of multicast data. Something must be done.
IGMP snooping
The Internet Group Management Protocol or IGMP is a way for switches to keep a list of multicast connections by looking at the packets themselves. Some more advanced switched support IGMP snooping, which in effect blocks multicast packets to devices that does not need them. This is an effective way to limit multicast packets in the network. Some switches implement this very well, others do not. When possible, keep away from IGMP snooping.
What is a VLAN?
VLAN or Virtual LAN is a way to keep certain network traffic separated from each other. For example, in a large company, you would want to keep all the network traffic from a development environment separated from a production department. This can be done by physically put the network on a separate switch, but what if network traffic needs to cross the entire building? To avoid a whole second network aside for regular data traffic, intelligent switches offer VLANs to communicate over a single connection, while having multiple logical network connections running.
How does VLANs work?
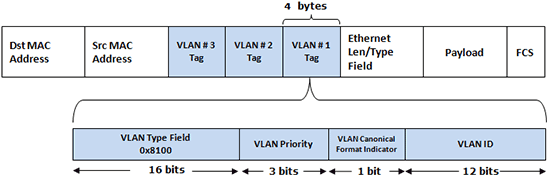
In the header of a IP packet, there is a field to assign a VLAN "tag" to the packet. By looking at the VLAN tag, switches can sort out what VLAN network a packet belongs to, and relay the packet to the correct ports. A standard network device does not have to support VLANs, and does not know how to deal with these. For instance, a DVD player will most likely have no support for VLAN tagging, while a NAS might! Managed Switches with VLAN support will have the feature to tag and untag VLAN traffic from and to a certain port, so that non-VLAN aware devices can communicate on a VLAN, without them even knowing.
Terminology
Because VLANs can be very confusing in setting up and maintain, some explanation should be given to terminology often used with VLANs:
- Ingress traffic - All network traffic entering the switch. This can come from any other network device: A computer, another switch, your network thermostat. If it sends packets towards your switch, it is considered ingress traffic.
- Egress traffic - All traffic going out of the switch.
- VLAN ID - The VLAN number that a network packet is tagged with. If it is not tagged or untagged, it is by default VLAN ID 1.
- PVID - Port VLAN ID. The VLAN ID default traffic on a port is tagged with. This will be explained later.
- Port based VLAN - VLANs are assigned to packets, based on the physical port on the switch. A very limited yet easily understood concept of VLANs.
- IEEE802.1Q - The protocol that facilitates VLANs
- Trunk port - Cisco uses this term to a port that communicates with another switch.
How to set up VLANs
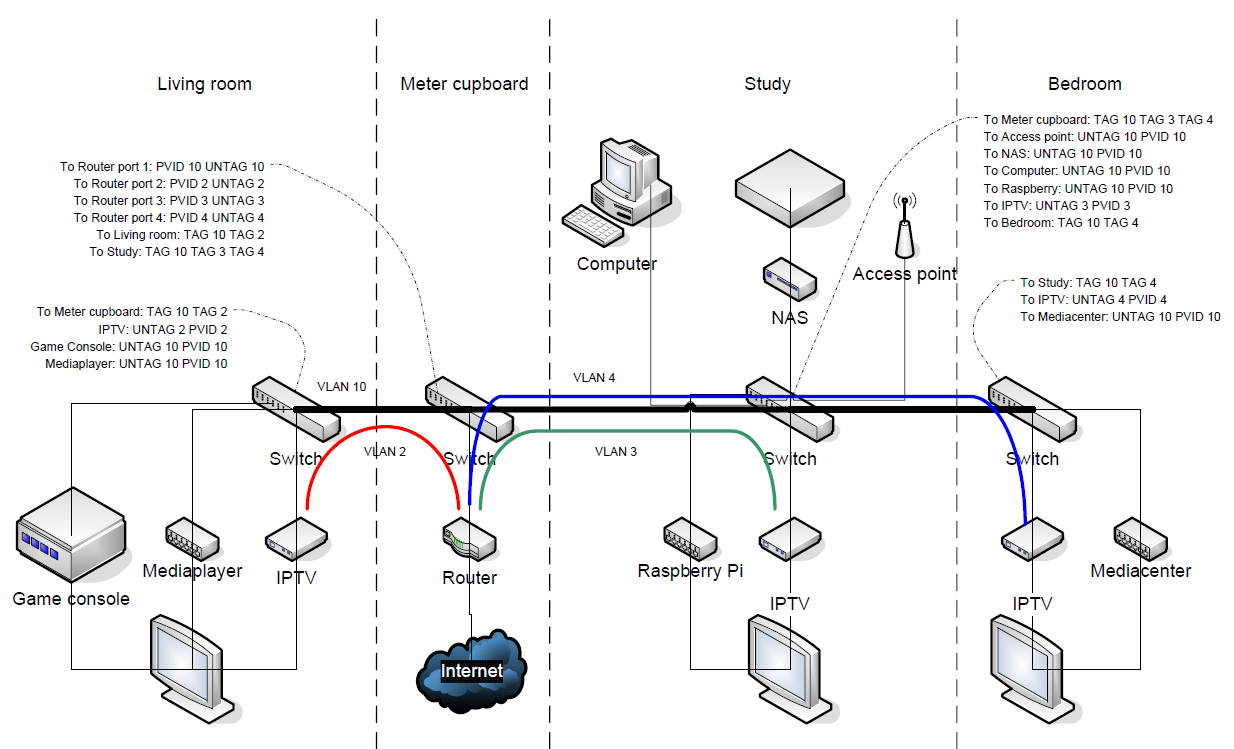
When setting up a VLAN network, create a different VLAN IDs for every separate network you want to have. In this example:
- Regular existing network - VLAN 10
- IPTV connection 1 - VLAN 2
- IPTV connection 2 - VLAN 3
- IPTV connection 3 - VLAN 4
You must create the appropriate VLAN ID's to every switch that will process network traffic of the corresponding VLAN. There is a maximum available VLAN ID's (4096) to the protocol, but the switch may have a limited amount of different VLAN ID's it can process. Simple managed switches will, for example, support only 32 out of the possible 4096. Still more than enough for our use. Now, for every port, you must define for every VLAN, how it will process EGRESS traffic:
- Exclude - The port will not be a member in the designated VLAN traffic.
- Tag - The packet will leave the switch on the port with the VLAN ID flag intact. If you want multiple VLAN ID's on a single connection (for example another VLAN aware switch or a device supporting VLAN ID's) you must set all VLAN packets to leave the switch tagged.
- Untag - The switch will strip the VLAN ID from the packet, and it will leave the switch as it was without VLAN. Logic defines that per port, only one VLAN ID can be set UNTAG.
If you set a port to untag a VLAN ID, you most likely would want all INGRESS traffic the same VLAN ID added, thus communicating with all other members of that VLAN. To accomplish this, set the PVID or Port VLAN ID to the appropriate VLAN that is set to UNTAG on that port. All outgoing traffic will have the VLAN tag stripped from the packet, while all incoming traffic will have the VLAN ID added to the packet.
VLAN switches
Of course, this advanced network capability comes at a price. Because these VLANs was almost exclusively used in large corporate networks, this capability was associated with large, expensive switches. Fortunately, smaller managed switches nowadays also support VLANs. To give some examples:
- TP-Link SG108E
- Netgear GS108Tv2
- HP 1820-8G
All of these are 8 port, managed gigabit switches.
New situation
With the improved setup in the new situation, separate VLANs are used to form a logical 1-to-1 connection from a IPTV box to the router. This way, no IPTV box will get mixed up with other traffic. You can further improve this by using QOS (Quality of Service) to all IPTV connections, giving them priority over regular network traffic. Because IPTV is a streaming connection, this is a good idea. If you are using the regular network connections to its full gigabit potential, IPTV will be uninterrupted due to this QOS setting.